firewalld-cmd Command Examples
The firewall-cmd command line tool lets you interact and manage the firewalld firewall in Linux. Here's how to use this command.


This tutorial will guide you into the world of firewalld commands, Linux's dynamic firewall manager. Whether you are a beginner looking to understand the basics or a seasoned system administrator looking to make the most of its advanced features, this guide is for you.
We'll start with the basics, explaining what firewalld is, how to install it, and which Linux distributions you can find it on. Next, I will walk you through firewalld-cmd commands for basic configuration, managing security zones, and allowing essential network traffic.
What is firewalld?
Firewalld is a dynamic firewall by Red Hat for Linux systems. This is a powerful tool that allows you to control network traffic entering and exiting your system. In other words, Firewalld acts as a security barrier that filters network connections, allowing only authorized ones and blocking potentially dangerous ones.
How does firewalld work?
Firewalld uses a zone-based approach to define different security levels. Here's how it works:
- Zones: Each network interface on your system is associated with a specific zone, such as "public", "internal", "work", etc. Each area has its own security rules. For example, the "public" zone may be more restrictive than the "internal" zone.
- Services: Firewalld uses preconfigured services (e.g. "ssh", "http", "https") to simplify configuration. You can assign services to zones, which allows you to specify which connections are allowed for each service.
- Custom Rules: If you have specific needs, you can also create custom rules to define specific firewall behaviors.
Installing firewalld
Now that you understand what firewalld is, let's move on to the next step: installing it in your distribution.
If you are using Fedora, Firewalld already comes preinstalled by default. So you don't need to install it. You can simply move on to setting up and using Firewalld.
RHEL and CentOS also come with Firewalld, but you can check if it is installed with the following command:
firewall-cmd --version
1.1.1
If you get output with Firewalld version, that means it is already installed. Otherwise, you can install it with the command:
sudo yum install firewalld
Or, if you're using CentOS 8 or higher:
sudo dnf install firewalld
On openSUSE, Firewalld is not always enabled by default, but you can install it using Zypper, the package management tool:
sudo zypper install firewalld
On Debian and Ubuntu, Firewalld is not included by default, but you can install it from the official repositories with the following command:
sudo apt-get update
sudo apt-get install firewalld
If you use Arch Linux, you can install Firewalld from the official repositories with the command:
sudo pacman -S firewalld
For Gentoo, you can install Firewalld using the Porting tool:
sudo emerge firewalld
firewalld basic configuration
Now that you have firewalld installed on your Linux system, it's time to move on to a basic setup.
Firewalld uses zones to define different security levels. Each network interface is associated with a specific zone, and each zone has its own security rules. Here are some common areas:
- public: This zone is typically used for untrusted networks, such as the Internet. Safety rules are generally strict here.
- internal: For internal and trusted networks, where the rules can be more permissive.
- work: Used for work networks, where security is important, but some flexibility is allowed.
- home: For home networks, where security is more flexible.
1. Show current zone
To view the zones currently associated with your network interfaces, use the following command:
sudo firewall-cmd --get-active-zones
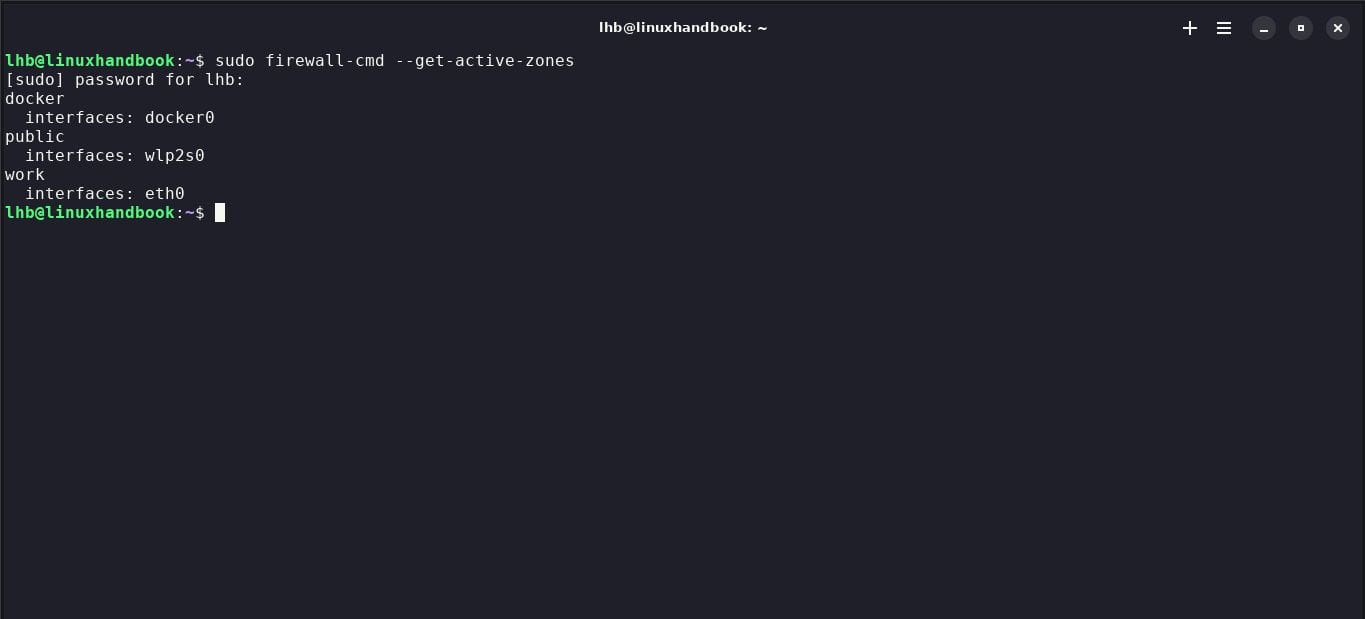
This will show you which interfaces are associated with which zones. In my case none.
2. Change the zone of an interface
If you want to change the zone associated with a specific interface, use the command --change-interfacefollowed by the interface name and the new zone. For example, to change the interface eth0to zone work, use:
sudo firewall-cmd --change-interface=eth0 --zone=work --permanent
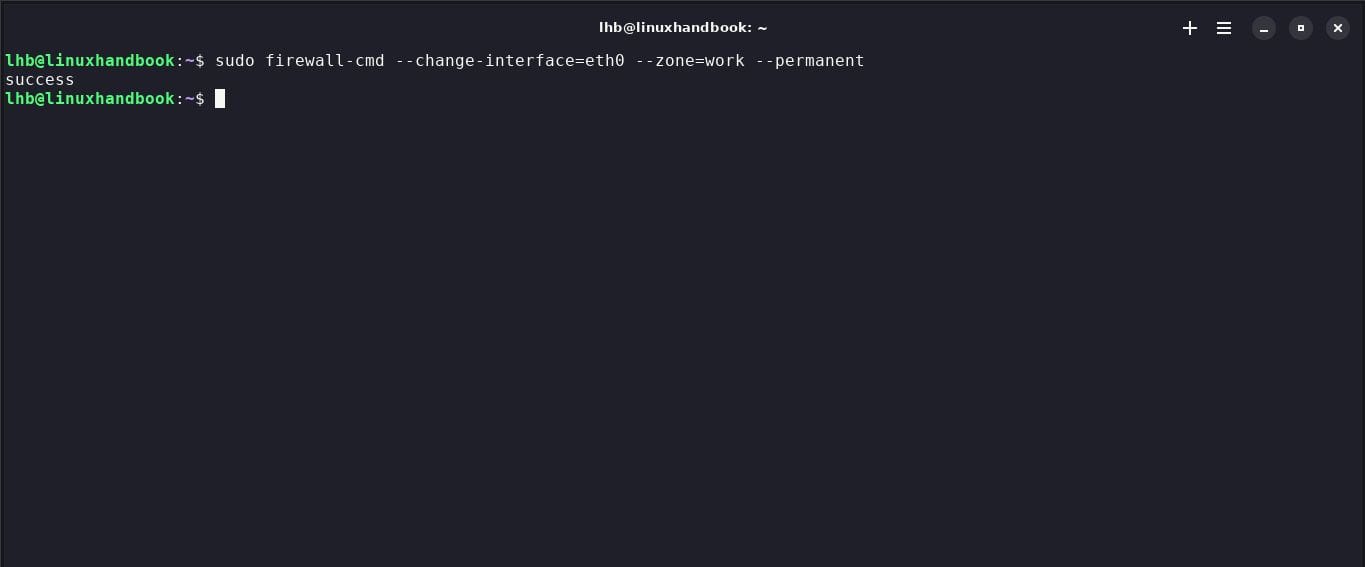
Make sure to add the option --permanentfor the zone to be persistent after reboot
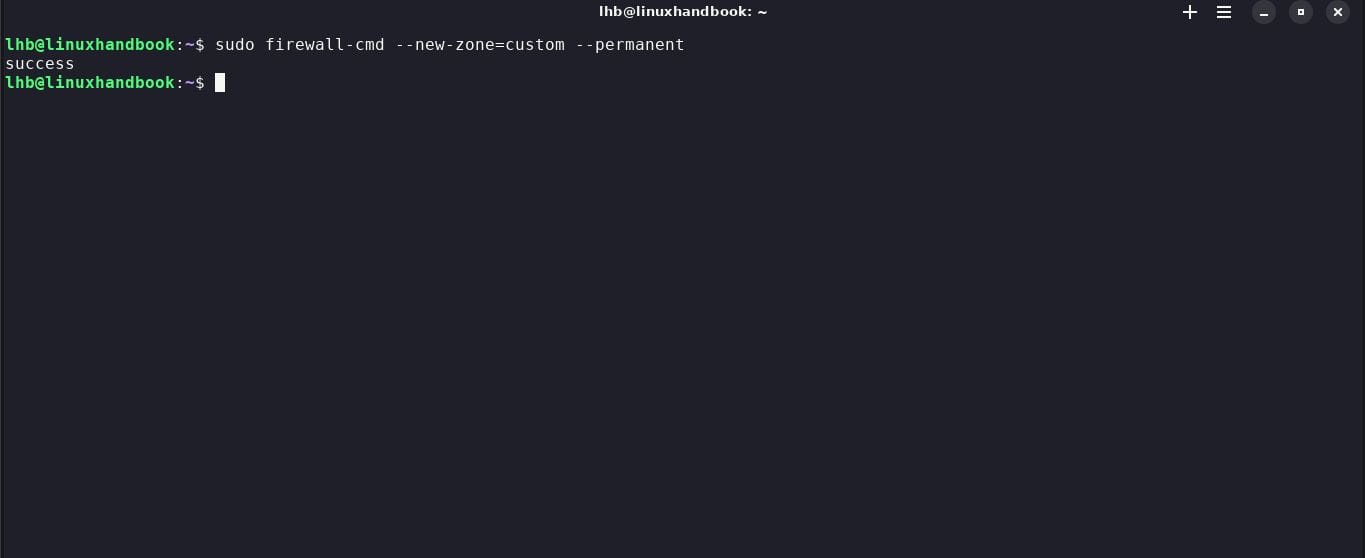
3. Create a new zone
You can also create a new custom zone with specific security rules using the command --new-zone. For example, to create a zone custom:
sudo firewall-cmd --new-zone=custom --permanent
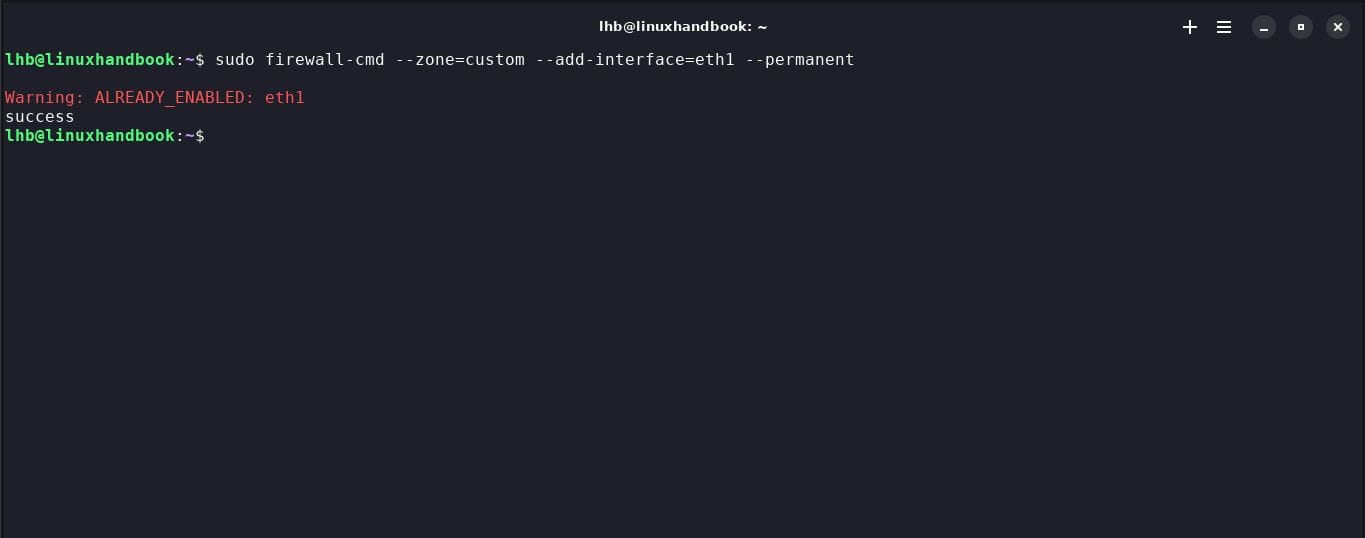
4. Associate an interface with a zone
To associate an interface with a specific zone, use the command --zone followed by the zone name and interface. For example, to associate the interface eth1with the zone custom, use:
sudo firewall-cmd --zone=custom --add-interface=eth1 --permanent
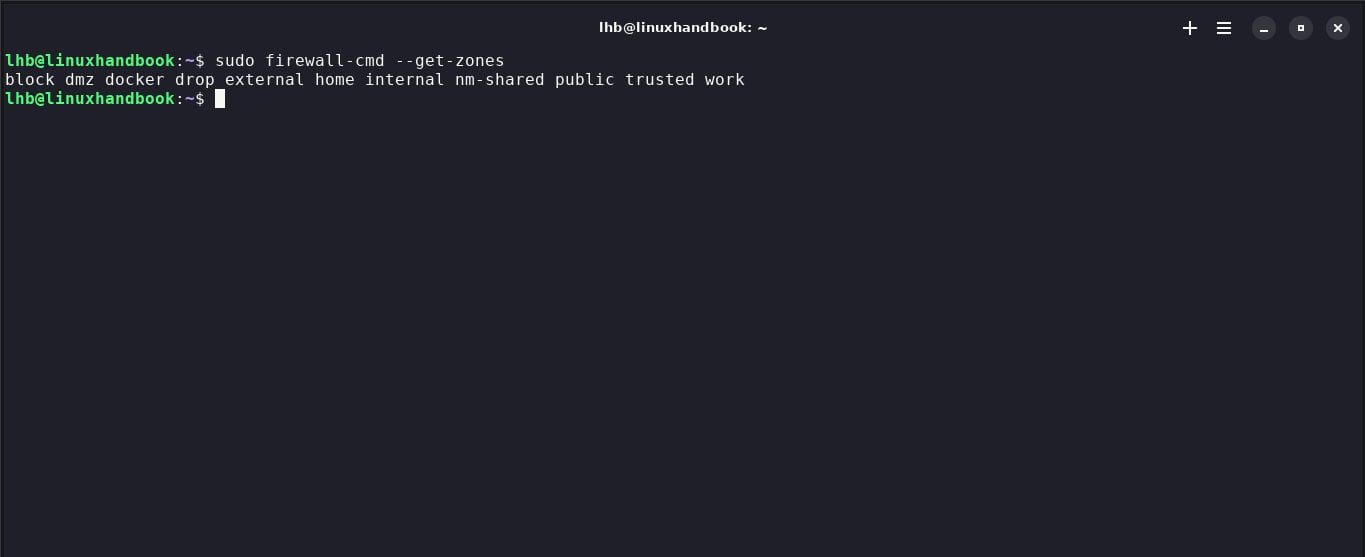
5. Get the list of all zones
sudo firewall-cmd --get-zones
6. Set default zone
You can set the default zone for your network interfaces with the following command:
sudo firewall-cmd --set-default-zone=work
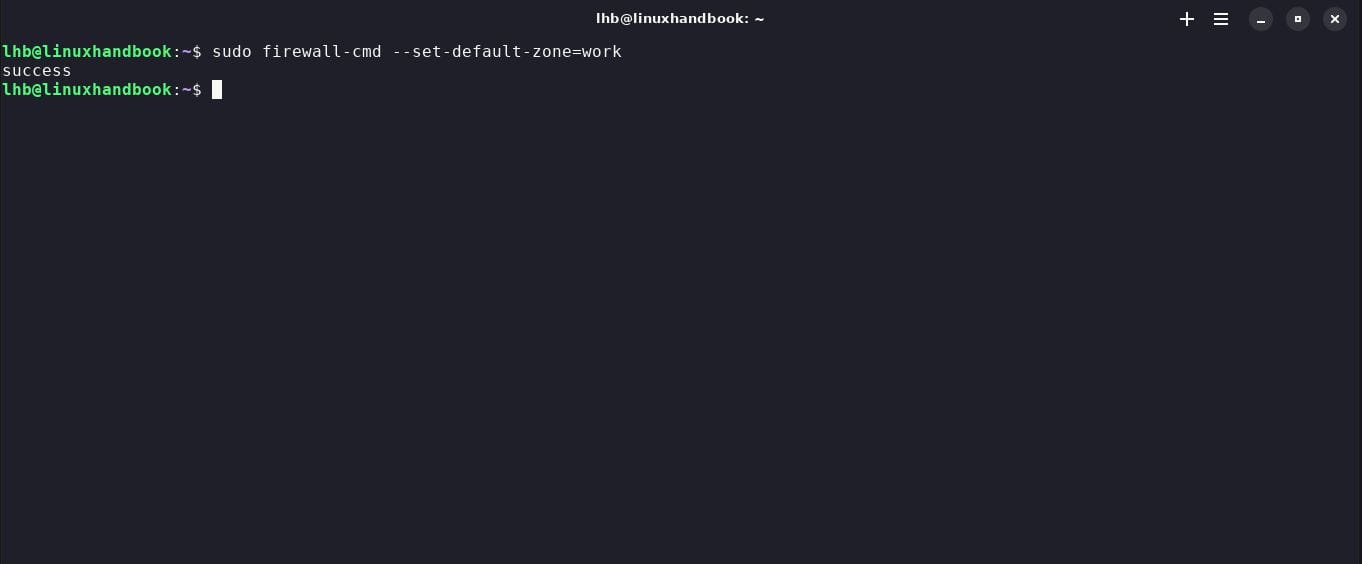
Make sure you choose the area that best suits your environment.
7. Allow essential traffic
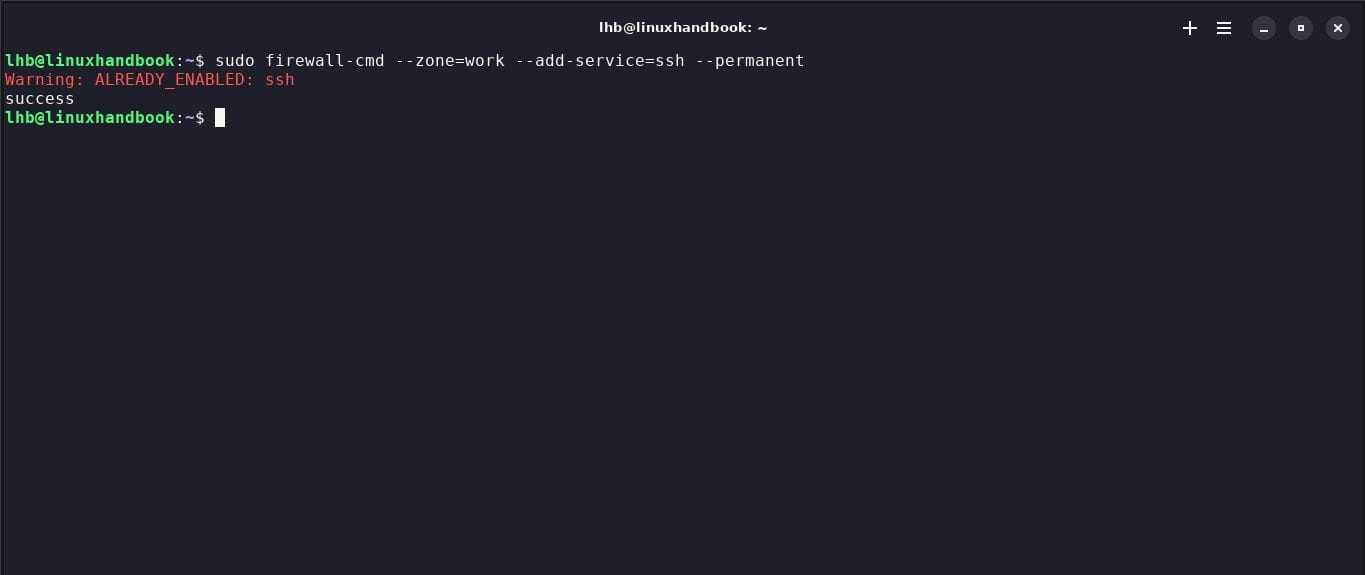
To enable essential traffic, such as SSH or HTTP access, you can use the command --add-service.
For example, to allow SSH, use:
sudo firewall-cmd --zone=work --add-service=ssh --permanent
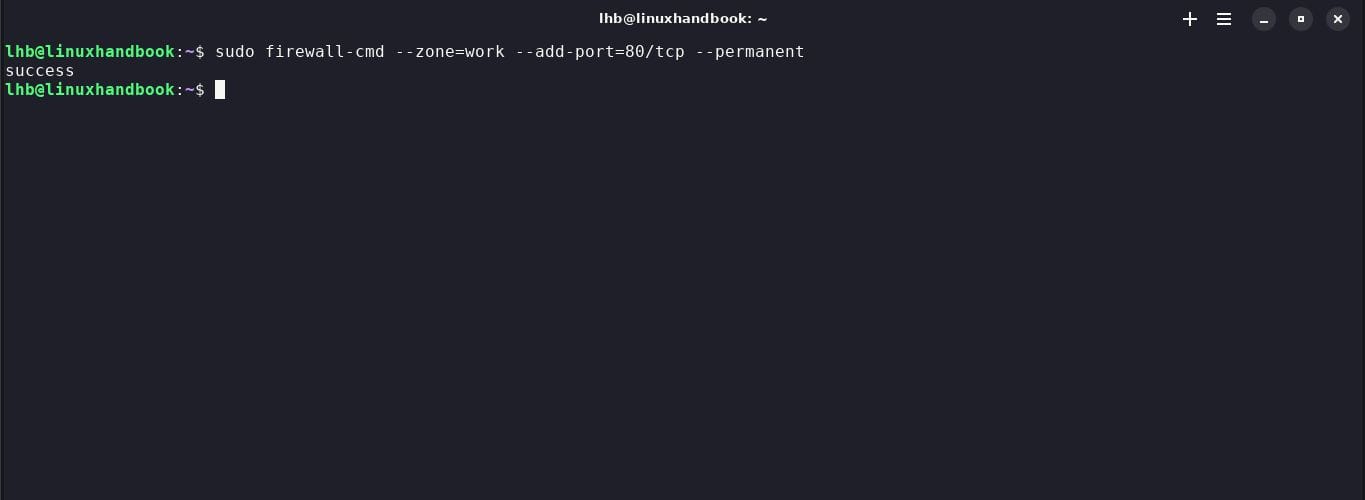
8. Open specific port
If you need to open specific ports, use the command --add-port. For example, to open port 80 for HTTP, do this:
sudo firewall-cmd --zone=work --add-port=80/tcp --permanent
9. Delete rules
If you made a mistake or need to remove a rule, use the --remove-serviceor command --remove-port, followed by the service name or port number.
Service management with firewalld
Understanding how to manage services is essential to controlling inbound and outbound network traffic accurately. We'll cover how to allow or deny access to specific services, which is crucial for the security of your system.
Services are specific applications or protocols that listen on particular ports. For example, SSH uses port 22, HTTP uses port 80, and HTTPS uses port 443. firewalld includes many preconfigured services to simplify policy management.
10. List available services
To display the list of available services, use the following command:
sudo firewall-cmd --get-services
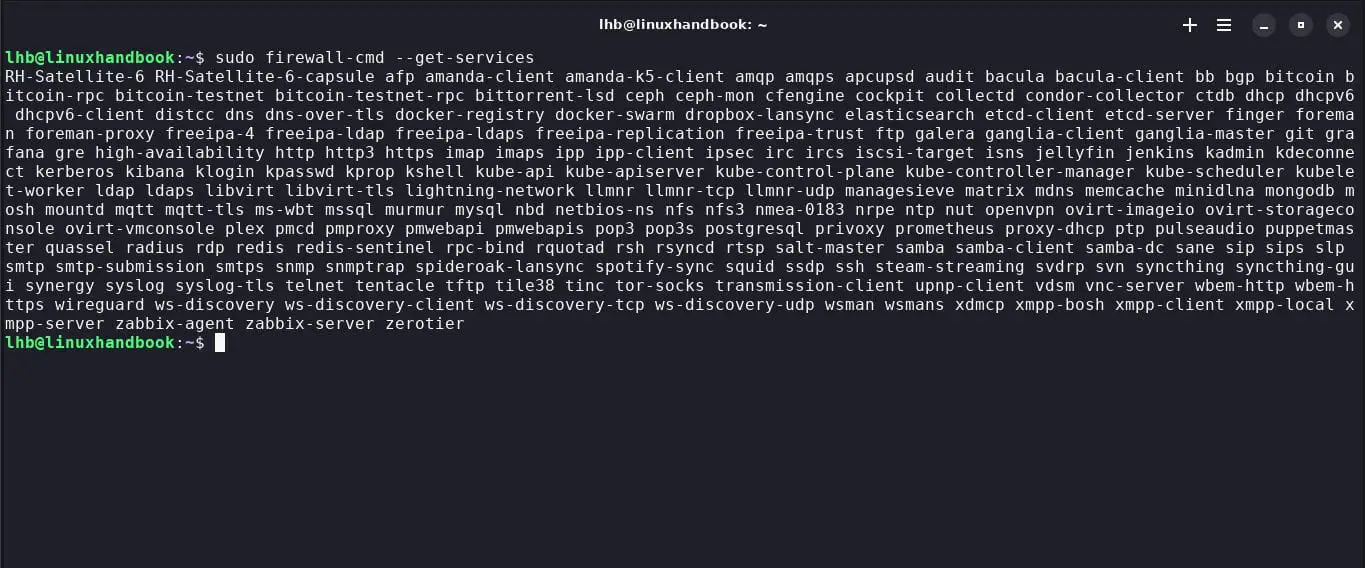
This will show you a list of services you can use in your rules.
11. Authorize a service
To authorize a specific service, use the command --add-service. For example, if you want to allow the SSH service, use the following command:
sudo firewall-cmd --zone=work --add-service=ssh --permanent
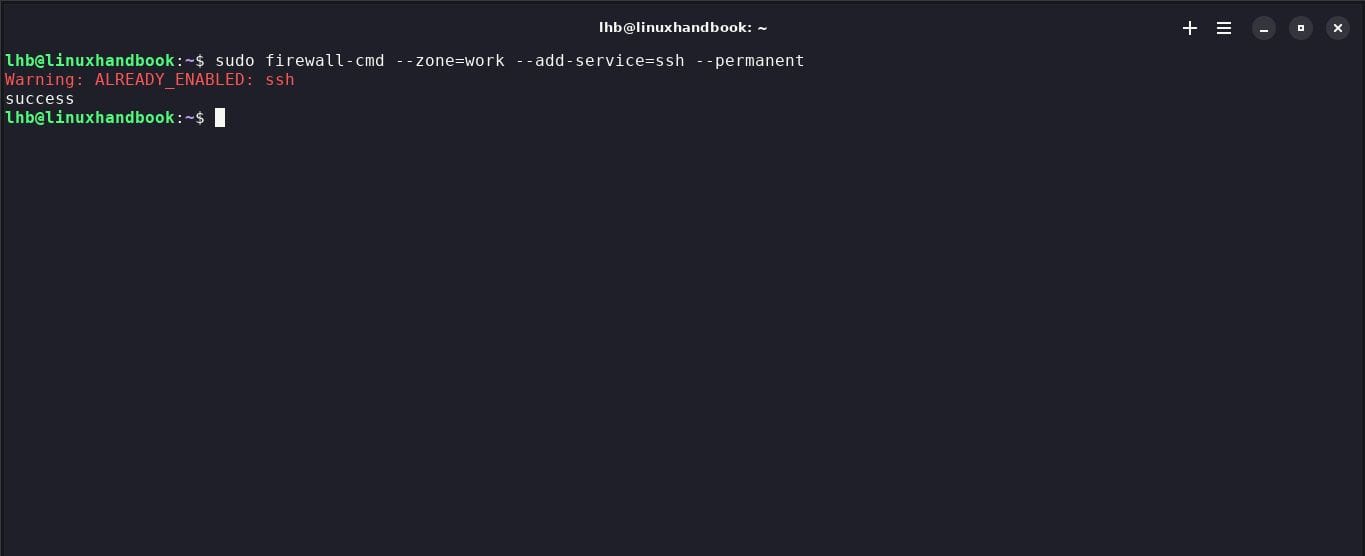
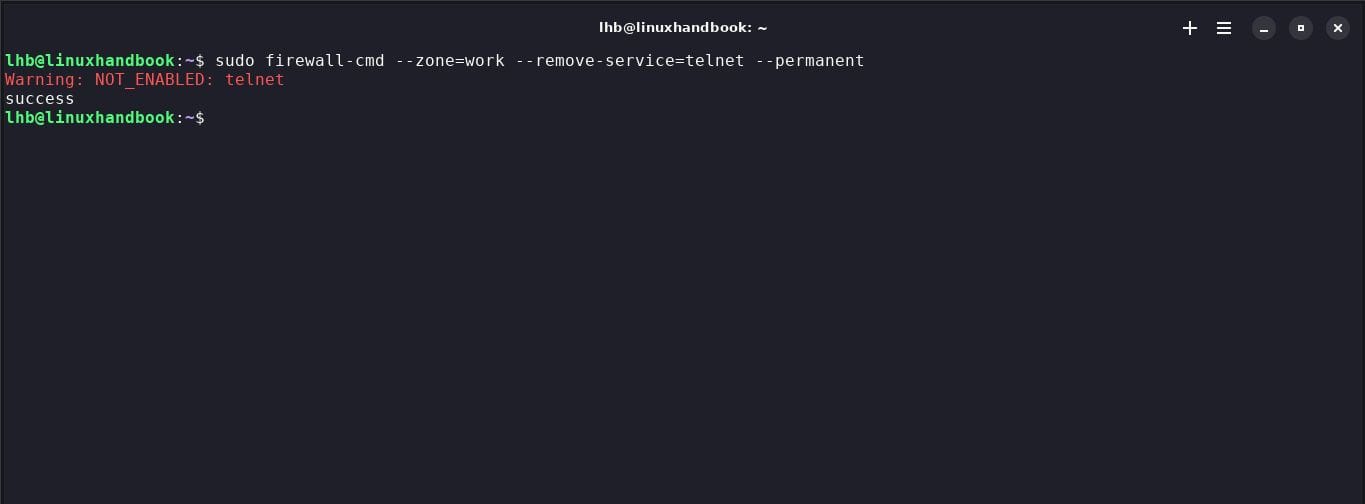
12. Refuse a service
If you want to deny access to a service, use the command --remove-service. For example, to deny Telnet service, use the following command:
sudo firewall-cmd --zone=work --remove-service=telnet --permanent
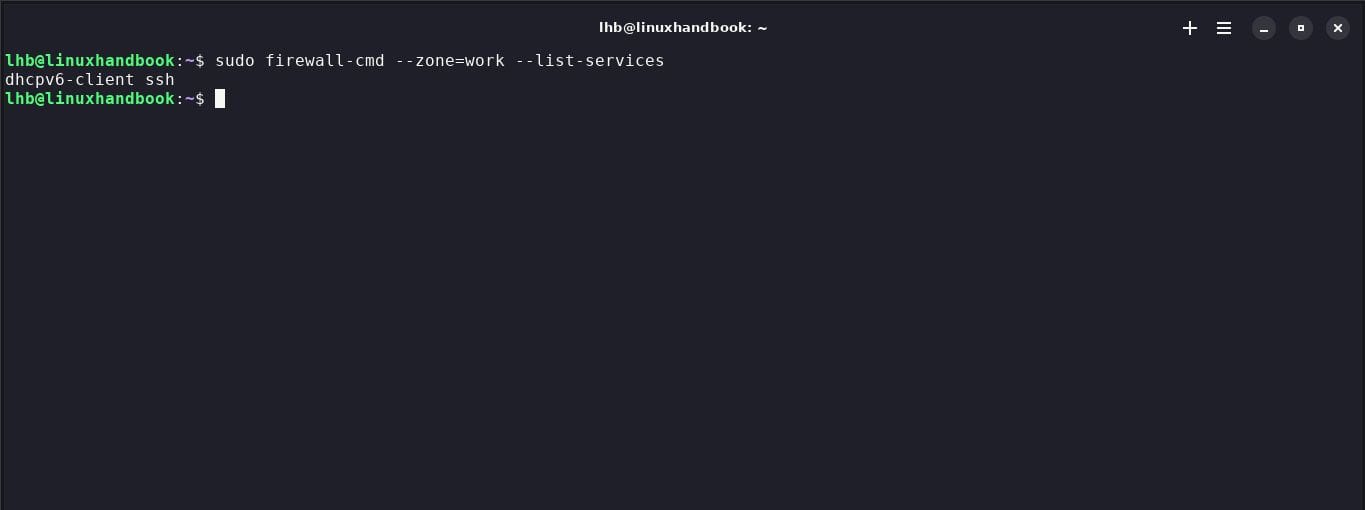
13. List of service sules
To view the list of currently active service rules, run the command:
sudo firewall-cmd --zone=work --list-services
This will show you the services you currently have access to in the specified area.
14. Customize service
If you need more specific rules for a service, you can create custom rules. For example, you can allow access to a custom port using the command --add-port. Make sure you understand your system needs before creating custom rules.
15. Apply changes
Once you have configured your service rules, don't forget to apply the changes with the command:
sudo firewall-cmd --reload
This will update the active firewall rules to reflect the service permissions or denials you have set.
16. Creating custom rules
Custom rules allow you to define precise firewall behaviors based on your needs. You can create custom rules using the command --add-rule. For example, to allow incoming traffic on a specific port, you can use:
sudo firewall-cmd --zone=work --add-rich-rule='rule family="ipv4" source address="192.168.1.0/24" port port="8080" protocol="tcp" accept'
This would allow inbound TCP traffic on port 8080 from source IP address 68.1.0/24.
17. Hide ports
To hide ports and prevent them from being detected by port scanners, you can use the command --add-rich-ruleto create a masking rule. For example :
sudo firewall-cmd --zone=work --add-rich-rule='rule family="ipv4" source address="0.0.0.0/0" port port="8080" protocol="tcp" drop'
This will hide port 8080 for all IP addresses.
18. Using add-ons
Firewalld supports various add-ons to extend its functionality. For example, the module conntrackhelps monitor and track network connections. You can activate a module with the command --add-module. For example :
sudo firewall-cmd --zone=work --add-module=conntrack
19. Active connection monitoring
To monitor active connections, you can use the command --list-connections. This will display a list of connections currently managed by Firewalld.
20. Event logging
Firewalld can log firewall events for later analysis. You can enable logging with the command --set-log-denied. For example :
sudo firewall-cmd --set-log-denied=all
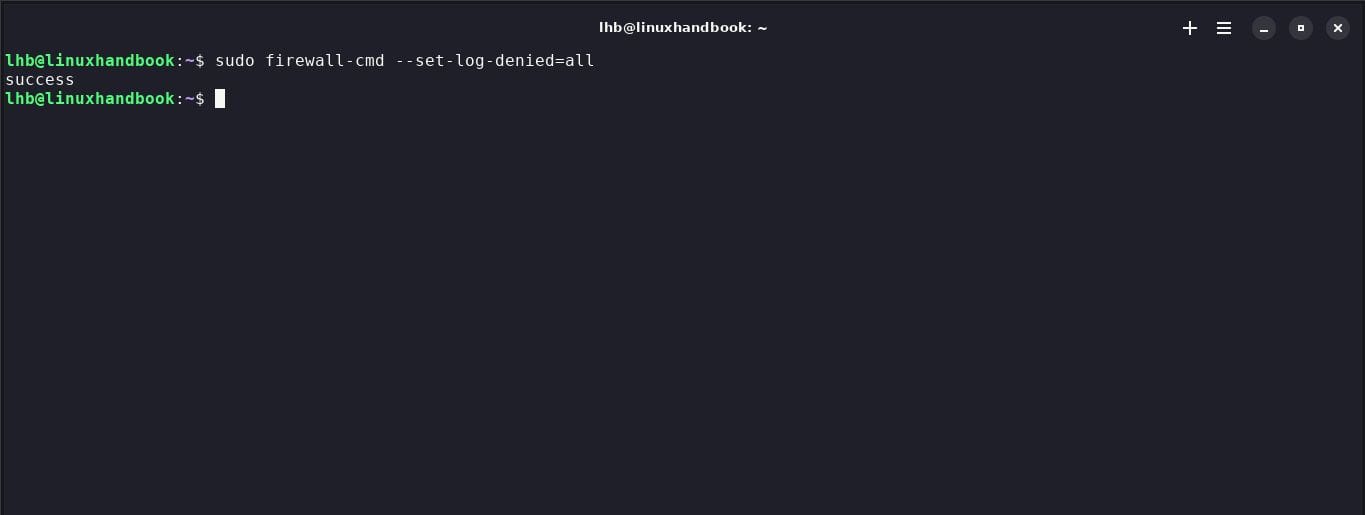
This will record all denial events in the log.
Troubleshooting tips for firewalld
Let me share a few firewalld examples that could help you in troubleshooting network issues arising from firewall.
21. Checking active rules
To view the currently active rules, use the command:
sudo firewall-cmd --list-all
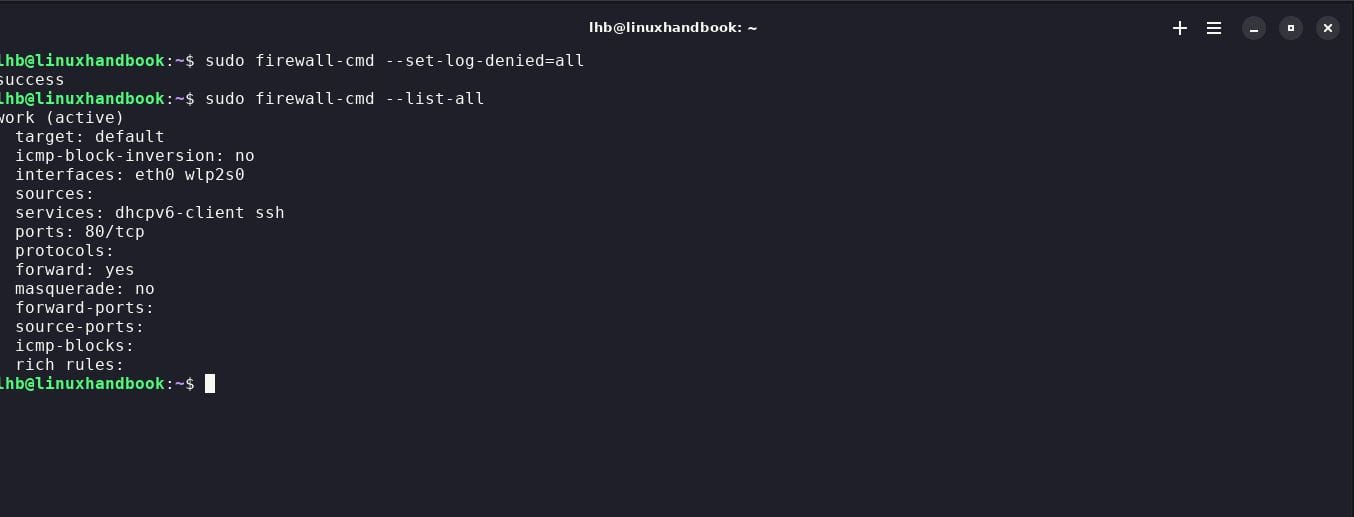
This will show you all the rules currently in effect, including zones, allowed services, etc.
22. Check firewalld logs
Firewalld logs are useful for troubleshooting. You can consult them with the command:
sudo journalctl -u firewalld
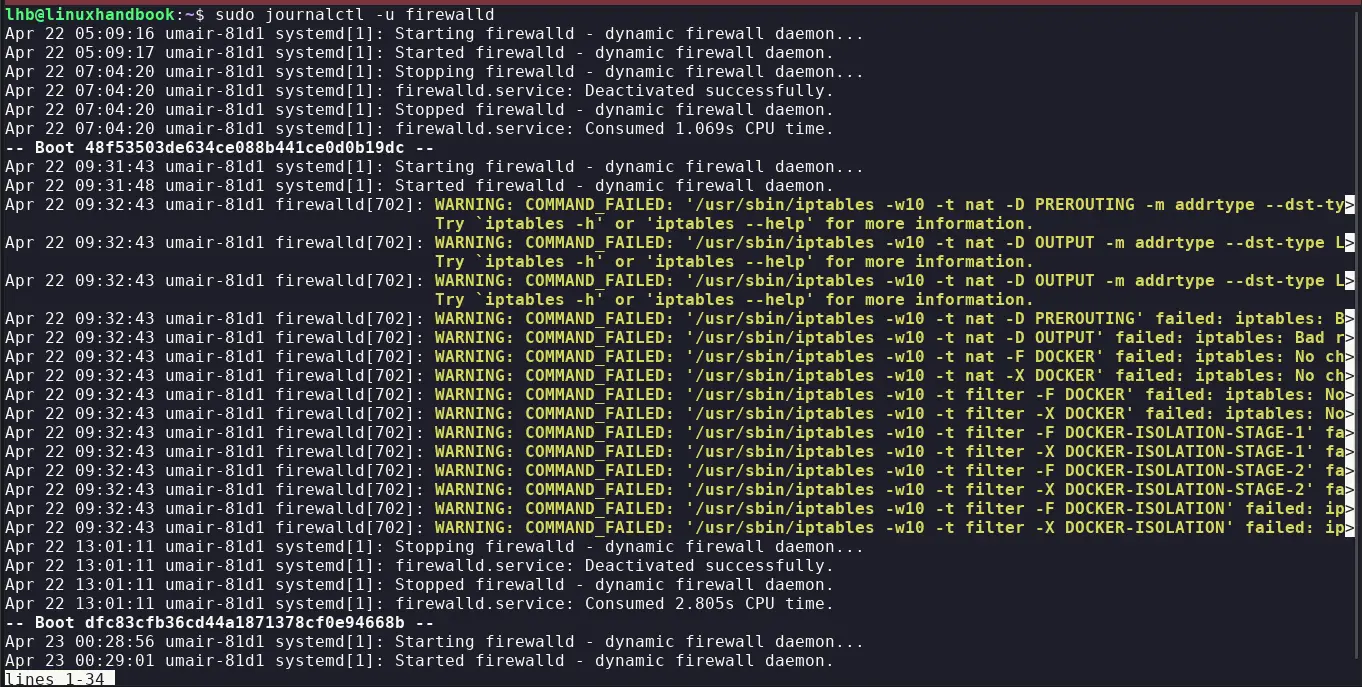
This will display logs related to Firewalld, which can help identify issues.
23. Add comments
When setting up complex rules, it can be helpful to add comments to explain their purpose. You can do this by adding --commentfollowed by the comment in the command. For example :
sudo firewall-cmd --zone=work --add-service=http --comment="Authorize HTTP Traffic"
24. Blocking IP addresses
You can add trusted IP addresses to firewalld exceptions or block unwanted ones.
To exclude a specific IP address (for example 8.8.8.8) on your server via firewalld, use the command:
sudo firewall-cmd --zone=public --add-rich-rule='rule family="ipv4" source address="8.8.8.8" accept'Check the zone to see if IP has been added to the exceptions in the rich rules:
sudo firewall-cmd --zone=public --list-all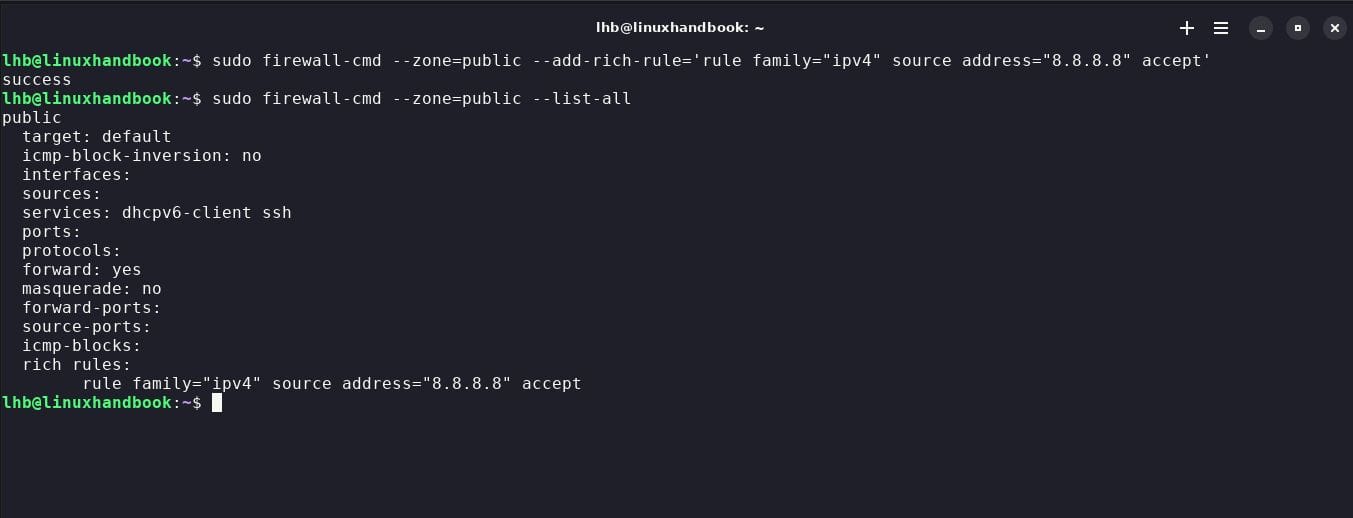
Final Words
That's it. With all this you are ready to secure your servers and your machines by filtering more finely and more securely the flows, services and ports for which we have complete confidence.
For those who still have doubts, it is always possible to use iptables rules.
About the authors
 LHB Community
LHB Community
LHB Community is made of readers like you who share their expertise by writing helpful tutorials. Contact us if you would like to contribute.
 Abhishek Prakash
Abhishek Prakash
Creator of Linux Handbook and It's FOSS. An ardent Linux user who has new-found love for self-hosting, homelabs and local AI.