Using SSH Port Forwarding as a Security Tool in Linux
Learn to configure SSH port forwarding on your Linux system. Remote forwarding is also explained.

Regular Linux users know about SSH, as it is basically what allows them to connect to any server remotely to be able to manage it via command line. However, this is not the only thing SSH can provide you for, it can also act as a great security tool to encrypt your connections even when there is no encryption by default.
For example, let’s say you have a remote Linux desktop that you wish to connect via SMTP or email but the firewall on that network currently blocks the SMTP port (25) which is very common. Through a SSH tunnel you would simply connect to that particular SMTP service using another port by simply using SSH without having to reconfigure SMTP configuration to a different port and on top of that, gaining the encryption capabilities of SSH.
Configure OpenSSH for port forwarding
In order for OpenSSH Server to allow forwarding, you have to make sure it is active in the configuration. To do this, you must edit your /etc/ssh/ssh_config file.
For Ubuntu 18.04 this file has changed a little bit so, you must un-comment one line in it:
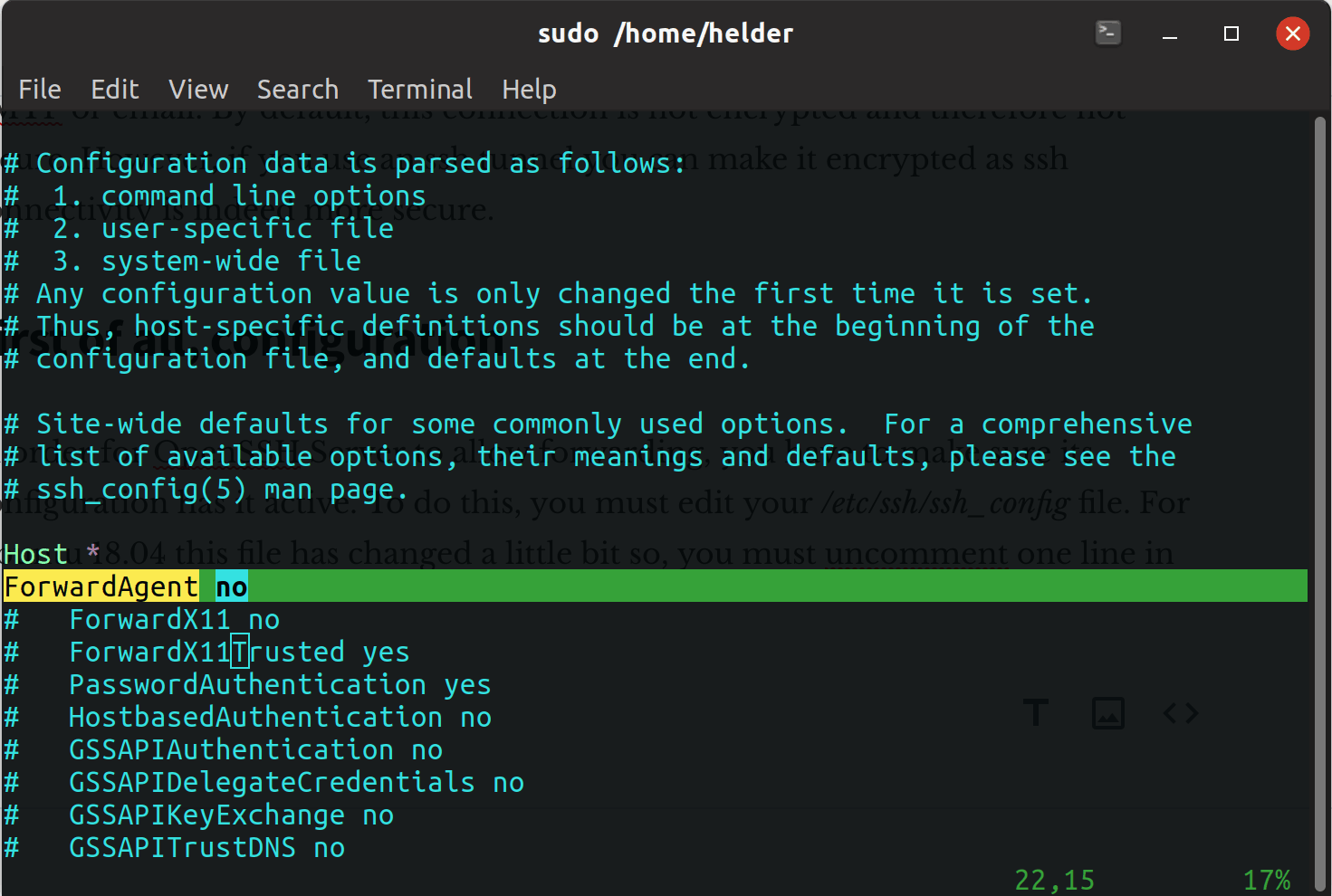
Once un-commented, you need to restart the SSH service to apply the changes:
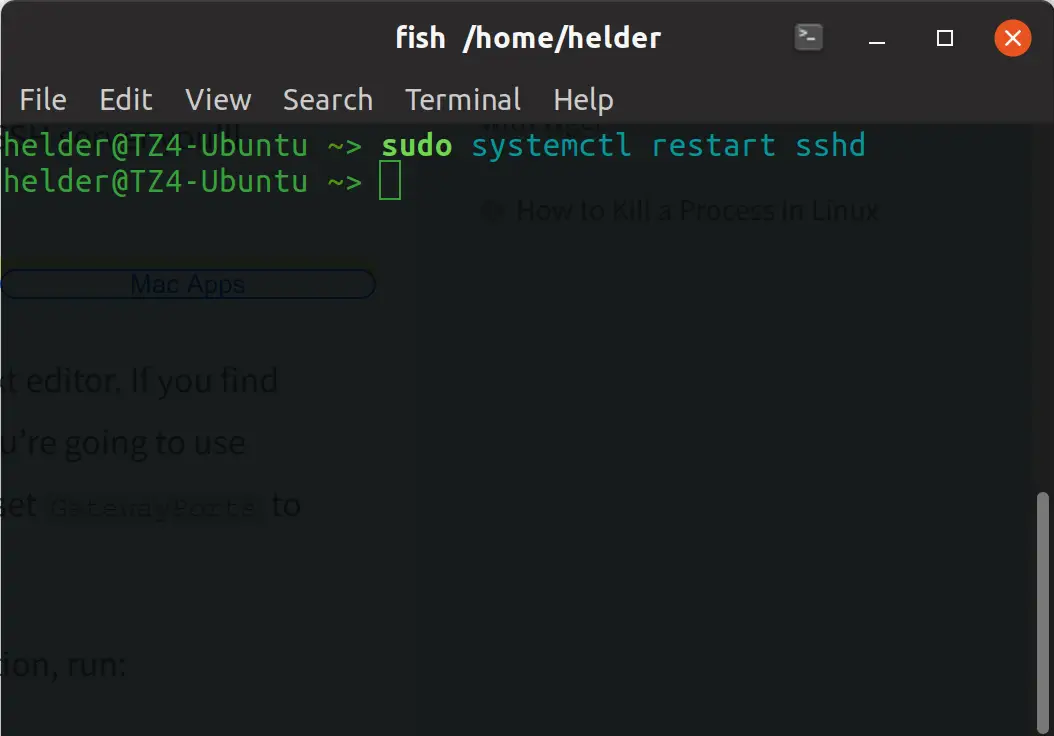
Now that we have our target configured to allow SSH forwarding, we simply need to re-route things through an open port we know is not blocked. Let’s use a very uncommonly blocked port like 3300:
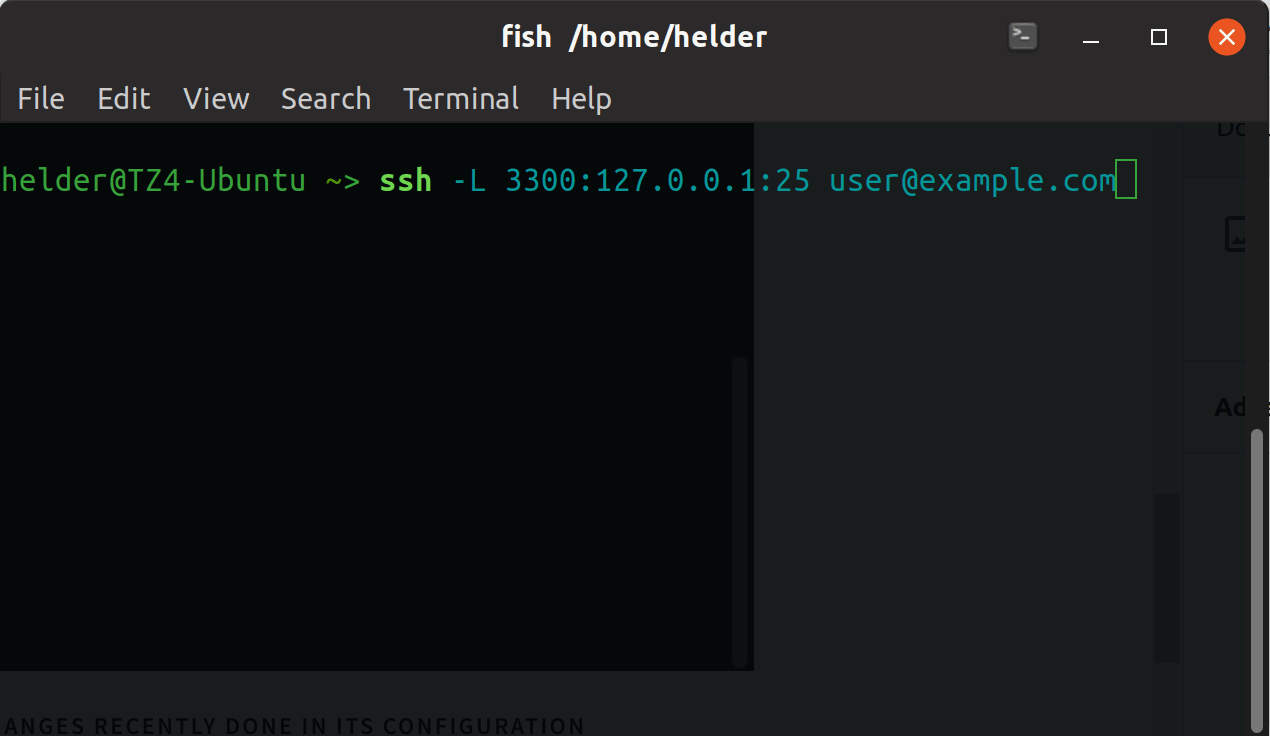
So now we have done this, all traffic that comes to port 25 will automatically sent over to port 3300. From another computer or client we simply will connect to this server to its port 3300 and we will then be able to interact with it as it was SMTP server without any firewall restrictions to its 25 port, basically we simply re-routed its port 25 traffic to another (non blocked) one to be able to access it.
The other way around: Remote Forwarding
We talked about forwarding a local port to another port, but let’s say you want to do it exactly opposite: you want to route a remote port or something you currently can access from the server to a local port.
To explain it easily, let’s use an example similar to the previous one: from this server you access a particular server through port 25 (SMTP) and you want to “share” that through a local port 3302 so anyone else can connect to your server to the 3302 port and see whatever that server sees on port 25:
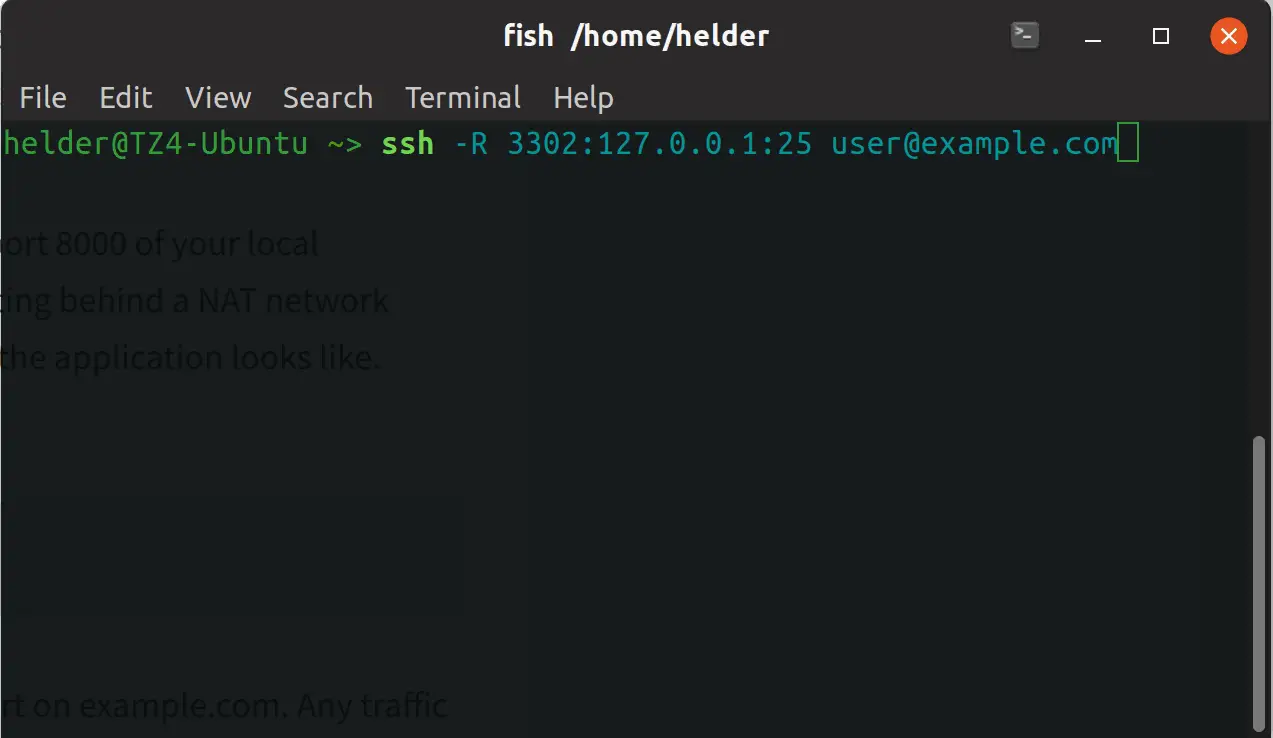
Summing up and some tips on SSH port forwarding
As you can see, this SSH forwarding acts like a very small VPN, because it routes things to given ports. Whenever you execute these commands, they will open SSH shells, as it understands you need to interact to the server via SSH. If you don’t need this, it will be enough to simply add the “-N” option in them, so they will simply not open any shell.
